iPurix
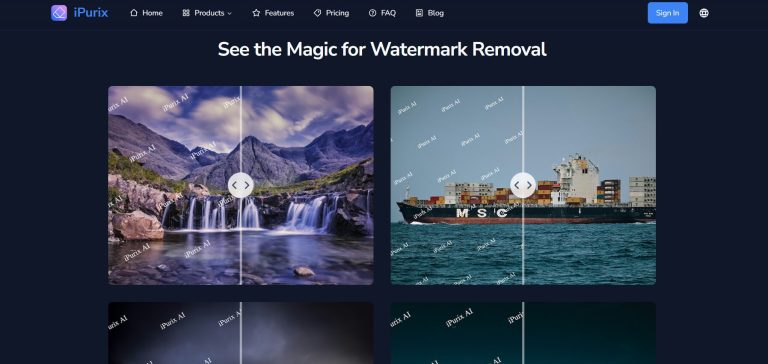
iPurix is an innovative AI-powered data security and privacy platform designed to protect sensitive information and enhance digital privacy for individuals and businesses. It leverages advanced artificial intelligence to proactively identify vulnerabilities, encrypt data, detect unauthorized access, and manage privacy settings across various digital environments. iPurix aims to simplify complex security protocols, provide robust protection against cyber threats, and ensure compliance with data privacy regulations.
Key Features & Capabilities
- AI-Powered Threat Detection: Proactively identifies and mitigates known and emerging cyber threats, including malware, phishing attempts, and ransomware, using behavioral analysis and machine learning.
- Intelligent Data Encryption: Automatically encrypts sensitive files and communications, ensuring that data remains secure both in transit and at rest, adapting encryption strength based on data sensitivity.
- Automated Privacy Management: Scans applications and online services for privacy risks, automatically adjusting settings to minimize data exposure and ensure compliance with user preferences.
- Smart Access Control: Utilizes AI to monitor and control access to sensitive data and systems, detecting unusual login patterns or unauthorized access attempts in real-time.
- Predictive Vulnerability Assessment: Forecasts potential security weaknesses in systems and networks, providing actionable insights to preemptively patch vulnerabilities and strengthen defenses.
- Real-time Data Anomaly Detection: Continuously monitors data flows for unusual patterns or suspicious activities that may indicate data breaches or insider threats.
- Secure Data Shredding: Ensures permanent and irreversible deletion of sensitive files, preventing data recovery even with advanced forensic techniques.
- Integration with Cloud Services: Seamlessly integrates with popular cloud storage platforms and productivity suites to extend security and privacy features to cloud-based data.
How to Use iPurix
While specific steps may vary depending on the platform, here’s a general overview of how to use iPurix:
- Installation & Setup: Install the iPurix application on your devices (computers, mobile phones) or integrate it with your enterprise systems.
- Initial Scan & Configuration: Run an initial scan to assess your current security posture and allow iPurix to identify sensitive data and potential vulnerabilities. Configure privacy settings according to your preferences.
- Define Protection Policies: Set up rules and policies for data encryption, access control, and threat response based on your security needs and regulatory requirements.
- Utilize AI Features: Let the platform’s AI capabilities automatically protect your data, detect threats, and manage your privacy in the background.
- Monitor & Review: Regularly monitor iPurix‘s dashboards for security alerts, privacy reports, and insights into your digital protection.
- Adjust & Optimize: Based on reports and evolving needs, adjust settings and policies within iPurix to continuously optimize your data security and privacy.
Common Use Cases for iPurix
- Individuals & Families: Protect personal photos, financial documents, communication, and Browse history from cyber threats and unauthorized access.
- Small to Medium Businesses (SMBs): Secure customer data, intellectual property, and financial records, ensuring business continuity and compliance with data protection laws.
- Enterprises: Implement comprehensive data loss prevention, advanced threat protection, and strict access controls across complex organizational networks and cloud environments.
- Remote Workforces: Secure data accessed and stored on personal and company devices used by remote employees, ensuring consistent security outside traditional office perimeters.
- Compliance & Regulatory Adherence: Helps organizations meet stringent data privacy regulations such as GDPR, HIPAA, or CCPA through automated policy enforcement and audit trails.
Frequently Asked Questions (FAQ)
Q: What is iPurix?
A: iPurix is an AI-powered data security and privacy platform that automates protection, encryption, and privacy management for sensitive digital information.
Q: How does iPurix use AI?
A: iPurix uses AI for advanced threat detection, intelligent encryption, automated privacy management, smart access control, and predictive vulnerability assessment.
Q: Is iPurix easy to use?
A: iPurix aims to simplify complex security and privacy tasks with an intuitive interface and automated features, making it accessible for a wide range of users.
Q: What are the benefits of using iPurix?
A: Benefits include robust protection against cyber threats, enhanced digital privacy, simplified security management, compliance assistance, and peace of mind regarding data safety.
Q: Does iPurix integrate with other tools?
A: Yes, iPurix typically integrates with cloud storage services, operating systems, and other enterprise security tools to provide comprehensive protection.
Q: Can iPurix help with data encryption?
A: Yes, iPurix features intelligent data encryption that automatically secures sensitive files and communications.
Q: Is iPurix suitable for small businesses?
A: Yes, iPurix is designed to be beneficial for individuals, small businesses, and large enterprises looking to enhance their data security and privacy posture.
Q: What kind of support does iPurix offer?
A: Support options may include online documentation, tutorials, in-app help, email support, and potentially premium customer support for business clients.
Explore and learn about File extensions
No results available
ResetReviews
iPurix has received 0 reviews with an average rating of out of 5
iPurix Website Information
- Category: AI, AI Image generator & Editor, Others
- Platform: Website
- License Type: Website
- Published: July 15, 2025
- Website: iPurix
Alternative version of iPurix
Alternative to iPurix
There are no similar listings
Reset